“Technology trust is a good thing, but control is a better one.”
Stephane Nappo
In today’s digital age, our lives are intertwined with technology. While its advancement has undoubtedly given us more convenient and efficient lives, it has also given us concerns. Statistics estimate cyberattacks happen every 39 seconds on average.
As we are getting more and more engaged in the digital world, we are creating wider exposure to the risk of being exploited by cybercriminals. These risks can arise from various sources and can have significant consequences.
Cybercrime techniques keep evolving, employing sophisticated methods to gain unauthorized access to our sensitive data. As much as this sounds scary, it is nothing new for us, but a modernized carriage road robbery. It is about crime like any other crime in terms of illegal activities and harm caused, with its specifics.
We will further explore steps on how you can achieve all the above in securing your digital assets from malicious actors.
Securing Your Digital Assets with Cybersecurity
Cybersecurity refers to the protection of computer systems, networks, and data from potential threats.
By developing a solid understanding of the risks in the digital world and best practices to prevent them, individuals and organizations can establish a strong foundation for protecting their digital assets.
· Cyber threats
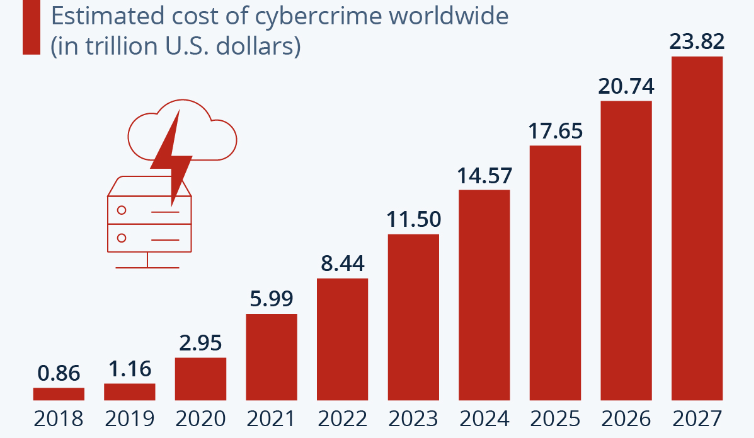
According to an ITRC report, the US ranked second in data compromises in 2022. Cybercrime is expected to grow in the upcoming years and it may not be possible to completely eliminate it. However, by understanding the threats and taking appropriate measures, individuals and organizations can better protect themselves against cybercrime.
There are numerous types of cybersecurity threats, each with its own characteristics and methods of attack:
- Malware: Malicious software designed to infiltrate systems, such as viruses, worms, Trojans, ransomware, and spyware.
- Phishing: A technique used to trick individuals into revealing sensitive information (such as login credentials or financial details) through emails, websites, or phone calls.
- Web-based attacks: These target vulnerabilities in websites or web applications to gain unauthorized access, inject malicious code, or steal sensitive data.
- Internet of Things (IoT) attacks: These compromise connected devices through security weaknesses to use them for botnets, data theft, or to gain unauthorized access to networks.
- Social engineering: Psychological manipulation of individuals to provide confidential information or perform actions that benefit the attacker.
- Distributed denial of service (DDoS) attacks: These overwhelm web servers or online systems to make them unavailable to their legitimate users.
- Insider threats: Malicious actions or data breaches caused by individuals within an organization.
- Advanced persistent threats (APTs): Sophisticated, long-term cyberattacks typically executed by skilled adversaries.
- Man-in-the-middle (MitM) attacks: These intercept and modify communication between two parties without their knowledge.
- Zero-day exploits: These target weaknesses in software or systems that are unknown to the vendor or have not yet been patched.
· Risk management
A risk assessment helps to identify potential cyber threats to your assets and allows you to prioritize efforts in establishing protection.
The main concepts involved in a risk assessment are:
- Asset identification
- Threat identification
- Vulnerability identification
- Impact evaluation
- Probability assessment
- Risk calculation
- Prioritization and mitigation
- Review and update
Remember that risk assessment is an ongoing process and cybersecurity is a continuous effort. It’s important to regularly reassess your risks, adapt your security measures, and stay vigilant in monitoring and addressing potential threats to your digital assets.
· Trusted service provider
Trusted service providers play a crucial role in ensuring cybersecurity for individuals and organizations. Before selecting one, it’s important to carefully evaluate who you rely on and do business with.
When selecting a cybersecurity service provider, it’s necessary to evaluate their expertise, experience, reputation, and alignment with your needs. Assess their range of services, customer reviews and references, certifications, and ability to provide tailored solutions to security challenges.
-
Wallet

How do you find a suitable wallet? The choice of the best wallet type depends on your needs. While considering these options, it might be helpful to compare Bitcoin vs. other cryptocurrencies to understand each blockchain network’s distinct security features.
Always download wallets from official sources and double-check the wallet’s website or app store listing to ensure authenticity. While hardware wallets tend to be the most secure option, it’s important to note that no wallet is entirely immune to all risks.
Other wallets, such as software and paper wallets, can provide adequate security when used correctly and appropriately. The process might differ depending on whether you are dealing with Bitcoin or another currency, emphasizing the importance of your initial comparative research.
· Trading platform database
An often-overlooked component in securing digital assets is the utilization of an ETF (Exchange-Traded Fund) database.
When looking for the best ETF database that suits your needs, focus on coverage and depth, analytical tools, and real-time updates. A platform with a rich set of tools and features, such as a drag-and-drop strategy builder, backtesting capabilities, real-time market data, and advanced charting, is a good choice.
Additionally, if your choice is supported by collaboration on cybersecurity habits between all stakeholders (investors, ETF issuers, and database administrators), you can call out “Bingo”!
· Security control practice
Multiple layers of security control create a robust defense against various types of threats. If you’re not sure where your organization stands in terms of cybersecurity, you can always hire a cybersecurity industry expert.
1.Strong passwords and authentication:
Passwords serve as the first line of defense in protecting your digital assets. Creating strong, unique passwords and regularly updating them is essential.
A good practice is to avoid using easily guessable passwords and instead make them more complicated by using a combination of uppercase and lowercase letters, numbers (7438309549575), and special characters (&^%$(*!@#$).
Additionally, implementing multi-factor authentication (MFA) adds an extra layer of security. MFA requires users to provide two or more forms of identification, such as a password and a unique code sent to their mobile device. In this case, if one factor is compromised, the other still ensures the security of your assets.
Organizations can use risk-based authentication, which only asks for extra credentials at a certain risk level. Instead of establishing a new authentication system, you can implement one of the existing online solutions.
2.Software and system update
Software and systems can be good, but never perfect. Hackers actively look for these imperfections to exploit them and gain unauthorized access or cause damage.
Continuous software development and the release of updates aim to address these imperfections. By regularly updating your software, you can improve system performance, add new features, and protect against vulnerabilities. Software updates often include security patches that address known vulnerabilities in the system.
3.Firewalls and antivirus software

Firewalls act as a barrier between your devices and the internet, monitoring and controlling incoming and outgoing network traffic. By implementing a firewall, you can filter out malicious traffic and prevent unauthorized access attempts.
Additionally, using reputable antivirus software can protect against malware, viruses, and other malicious programs. Regularly update and scan your devices to ensure optimal protection. In organizational systems, involving a third party can help with advanced-level scanning of your IT environment.
4.Data encryption
Data encryption is a great technique for protecting sensitive information. Encryption converts data into an unreadable format so that unauthorized individuals cannot decipher the information without the encryption keys.
It’s recommended to implement encryption for data at rest, in transit, and in use. This can be especially important when data is stored in the cloud or transmitted over networks.
5.Data backup
Data loss can have severe consequences, ranging from financial loss to reputational damage and identity theft. To protect against data loss, ensure that backups are performed at regular intervals and stored in secure, off-site locations.
Cloud-based backup services can provide an added layer of protection, allowing for easy restoration of data in the event of a cyber incident or system failure.
6.Compliance and regulations
Many industries and jurisdictions have established cybersecurity regulations and standards to protect sensitive information and maintain the privacy of individuals.
Some of the compliance standards that you may need to focus on include the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and the California Consumer Privacy Act (CCPA). If you’re not sure where your organization stands in terms of compliance, you can always hire a cybersecurity industry expert
7. Education and training
Develop comprehensive training programs that cover topics such as identifying phishing emails, recognizing suspicious websites, and practicing safe browsing habits. Encourage users to promptly report any potential security incidents.
Human error remains a significant factor in cybersecurity breaches. A report from last year showed that 82% of data breaches involved a human element. By fostering a culture of cybersecurity awareness, individuals can become an active line of defense against cyber threats.
· Incident response

There is no such thing as a 100% guarantee in the world of cybersecurity. Despite preventive measures, incidents can still occur.
Companies such as ChatGPT, Reddit, T-Mobile, Western Digital, Twitter, and WhatsApp have all experienced incidents affecting hundreds of millions of users. In some cases, companies even added to the burden by covering up the incident.
Incident response involves having a well-defined plan to detect, respond to, and recover from security incidents. Depending on the affected party:
- For individuals: Identify the breach, contain it (e.g., change passwords, disable compromised accounts, or disconnect affected devices from the network), notify relevant parties (such as service providers), secure personal devices, monitor accounts, report any unauthorized transactions or identity theft immediately, and seek professional assistance.
- For organizations: Have an incident response team in place, identify the incident, contain and mitigate it, notify and communicate with relevant parties, investigate the incident, conduct a post-incident analysis and make improvements.
A well-prepared incident response plan can minimize damage, reduce downtime, and aid in the investigation and prosecution of cybercriminals.
· Safety drill brief
By understanding the principles of cybersecurity, conducting risk assessments, implementing strong passwords and authentication measures, keeping software and systems updated, utilizing firewalls and antivirus software, educating users, encrypting sensitive data, and regularly backing up your data, you can significantly enhance the security of your digital assets.
Empower yourself with knowledge and good practices, and choose wisely when managing your digital assets. Remember that cybersecurity is an ongoing process, so staying up to date is a high priority.
With these proactive steps, you can safeguard your assets and navigate the digital landscape with confidence.