Documentation of evidence is critical in the compliance and audit process. . Be it any compliance audit performed including SOC1/SOC2, documenting the evidence is crucial for demonstrating compliance. Organizations will have to provide documents suggesting and highlighting the policies, procedures, processes, and measures implemented are in line with the compliance requirements. These documents are formal evidence that should be submitted to the auditor for verifying your organization’s compliance status.
The documents that you are required to provide as evidence will depend on the type of audit your organization is undergoing. So, for instance, if your organization is undergoing SOC1 Audit will require documents relevant to internal controls relating to the financial reporting. Elaborating more on this we have today shared a list of documents that your organization may have to provide the auditor for conducting the SOC1/SOC2 Compliance audit process. So, let us take a closer look at the kind of documents required as evidence for the audit process.
Gathering Documents as Evidence for SOC1/SOC2 Audit
Documents as evidence are essential for your organization to achieve and maintain compliance with SOC1/SOC2. As a part of your preparation for an upcoming compliance audit, you will have to have in place a list of documents that are expected to be provided to the auditor.
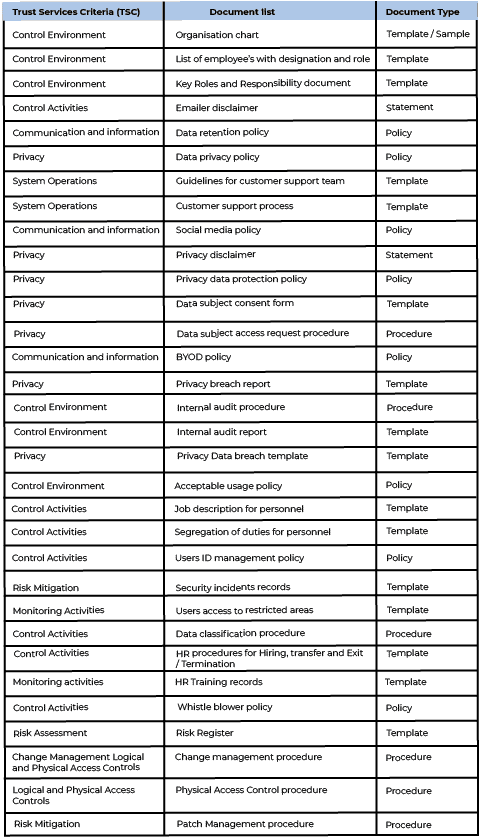
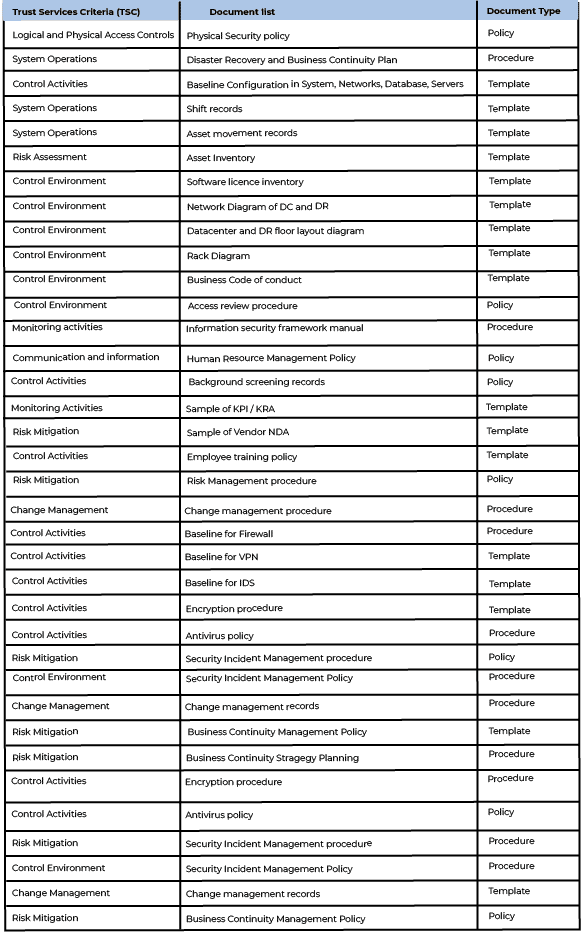
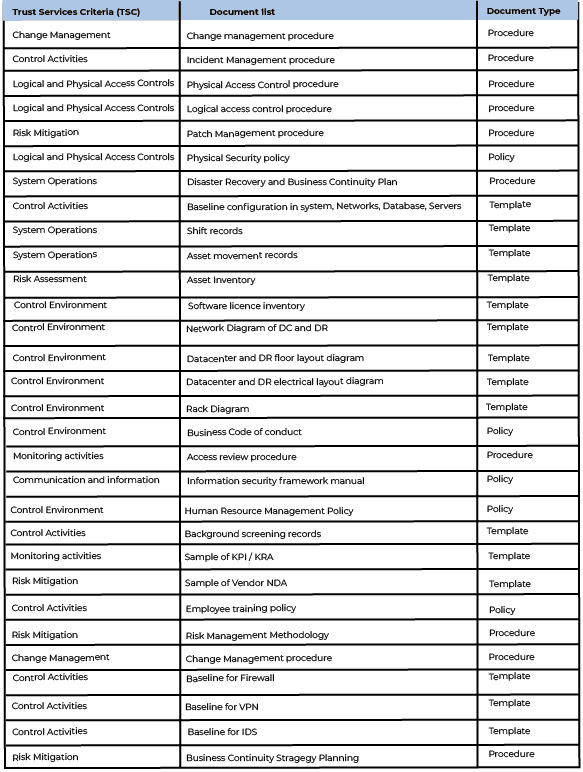
The list of documents that you provide will most likely enhance your chances of completing the audit. These documents that serve as evidence will further allow the auditor to conduct the audit efficiently. This way auditors too will have a better understanding of your business operations, systems, and infrastructure. So, here is a checklist that your organization can refer to when documenting evidence for providing the auditor before the SOC1/SOC2 Audit.
Management Description
Management description is a document to be given by your organization to the auditor before initiating the audit process. The document comprises a detailed description of your organization’s system pertaining to your organization’s processes, operations, infrastructure, and controls. These are system controls that facilitate your organization to provide services committed to clients and ensure Security, Availability, Processing Integrity, Confidentiality, and Privacy of business data. It is also important to note that the Management Description provided to the auditor must be updated if the process changes during the course of the engagement.
Complementary User Entity Controls
Complementary user entity controls are operative measures implemented at the user-entity level within your organization (service organization). This refers to measures implemented to secure outsourced services from other businesses such as financial auditing, cloud services, or transactional services from another business. Your organization must provide the auditor details indicating complementary user entity and service commitments that are key to your organization. This helps align the reports with the control objectives.
Technical Security Documents
Your organization must have in place documents comprising a list of physical inventory of all devices on your network, equipment maintenance records, and information related to security plans and measures. This includes details such as system configurations, data retention, and destruction policies, policies for outsourced application development, acceptable access, and usable policies, encryption policies, implementation requirements, and password requirements to name a few.
The document must also include records of access logs, system backup logs, system update logs, patch records, and key security controls protecting customer data. Your organization must document any data and documents relating to the implementation and management of infrastructure security controls.
Operational Documents
Your organization must also have in place operational documents including systems control documents, data flow diagrams, details of risk management programs and plans, compliance programs, and privacy documents such as privacy practices, data use agreements, unsubscribe, and opt-out policies, and confidentiality agreements.
Human Resource Documentation
Human resources documents include having in place organizational chart, list of roles and responsibilities of every employee related to compliance process positions, employee handbook, access levels of employees security awareness training logs, policies, procedures, and processes for hiring and onboarding new employees, evaluating employee performance, formal process for employee termination, evidence of removing the physical and system access for terminated employees, disciplinary action for violations of company policy, change of position or inter-department transfer within the company. The HR documents must also include policies, standard operating procedures and Information Security Policy, Code of Conduct, Corporate Governance Manual, and HR Manual.
Administrative & Security Policies
Organizations must have in place administrative policies related to their security program including Information Security Policy, Business Continuity Policy, Incident Management Policy, Disaster Recovery Policy Process and Logs, Data Classification Policy, Logical and Physical Access Policies & Procedures, Change Management Policy to name a few.
Third-Party and Vendor Contracts
Your organization must also have in place all documentation associated with third-party companies, contractors, and service providers. This includes having in place a Business Associate Agreement (BAA), Service Level Agreements (SLAs), and other Vendor & Third party Contracts and Agreements.
Risk Assessment and Other Audit Documents
Your organization must also document previous compliance assessments, risk assessment reports, audit reports, third-party audits, self-assessment questionnaires, documents with a list of gaps identified in previous audits, remediation and corrective action plans, reports of penetration tests, vulnerability tests, and such other risk assessment.
Conclusion
Compliance audit involves large quantities of documentation and evidence requirements to be provided to auditors. Your organization should have a central repository with all necessary documents easily available to your auditor. This way your organization will also know about the missing documents required for building evidence and for a successful audit process. Further, reviewing the documentation evidence in the central repository will give your organization the time to address the gaps in the documentation requirements and ensure the fulfillment of evidence requirements for a successful audit process.
Just to ensure a systematic audit process we recommend you consult a qualified auditor and consultant who can guide you through the audit documentation and assessment process. For any assistance and guidance in SOC1/SOC2 Audit & Attestation, you can contact our experienced and qualified consultants at VISTA InfoSec. Our team of auditors and consultants can guide you and walk you through the entire audit process to ensure the audit is a success for you.